E-government means the use of internet technology as a policy for exchanging information, providing delivery of public services and transactions with citizens, businesses and other arms of government. The most expectations for e-government are improved efficiency, convenience, and better accessibility of public services.

Malaysia’s e-government initiative starts in 1997 with the launch of the Multimedia Super Corridor’s E-Government Flagship Application. The vision for Malaysia government is to enable government to become more responsive and refills the needs for its citizens.
The seven pilot projects of the Electronic Government Flagship Application are:
1. Project Monitoring System (SPP II) - PMS project provides the new system for development projects observation. Scope of this project comprises 3 aspects (application, data, and communication) that aim to increase the efficiency and effectiveness of project management.
2. Human Resource Management Information System (HRMIS) - HRMIS is an integrated, technology-enabled Human Resource Management Information System for the Malaysian Public Service, incorporating Global Best Practices in HR that would enable the Public Service to successfully deal with the Challenges of the K-Economy.
3. Generic Office Environment (GOE) - great document and office management solution that enables users to effectively and efficiently handle their office environment. It is fully web-based and has been customized based on local developed package, DRDok.

4. Electronic Procurement (EP) www.eperolehan.com.my/– end-to-end electronic procurement system that enables Government Agencies around the country to procure products and services electronically from both local and international suppliers. E-Procuremeent transaaction value grew in 2006: RM 2 Billion worth of contract
5. Electronic Services (E-Services) http://www.eservices.com.my/- Provide perform transactions with various service supplier example Jabatan Pengangkutan Jalan (JPJ), Polis DiRaja Malaysia (PDRM), Polis DiRaja Malaysia (PDRM), Tenaga Nasional Berhad (TNB)

6. Electronic Labour Exchange (ELX)http://www.elx.gov.my/ - Electronic Labour Exchange captured 300,834 job seekers, 1,544,881 vacancies and 823,430 job matches
7. E-Syariah http://www.esyariah.gov.my/ - integrated with the Muslim Marriage System
Now goverment already provide 3,749 Government forms can be downloaded for free and 1,174 online services are available on the Portal.
The Problems faced by e-government are information infrastructure, efficiency, quality of service, lacks of public awareness ,language barrier and public administration. Government still not enough effort put for awareness.Many citizens do not use e-government for several reasons, amongthese unfamiliarity with ICT, lack of access, lack of training, and concerns about privacy and security of information.
So E-government may provide easy and convenience in the delivery of public services, and offer innovative government services that will prompt citizens.



















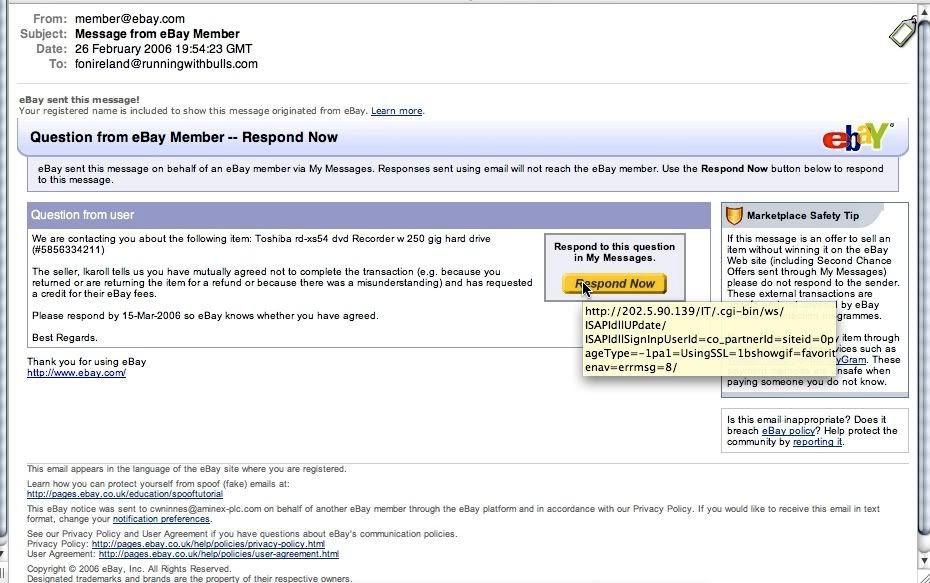
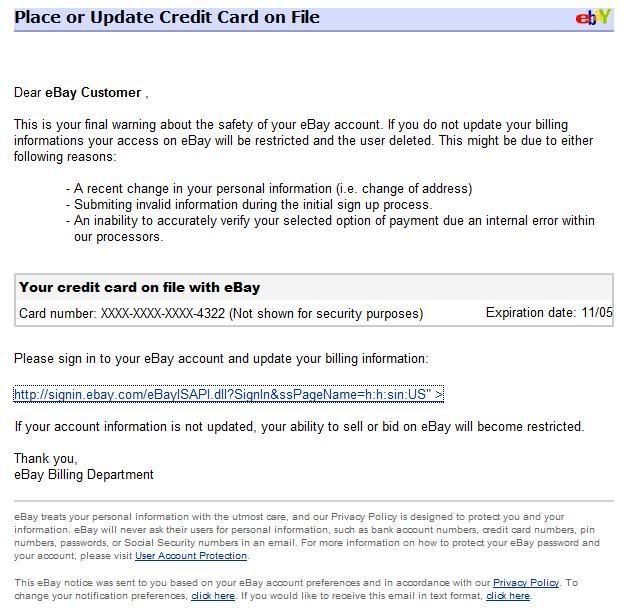 Look at the link here. It looks as valid as it could. It is written http://signin.ebay.com, but this written link actually points again, yes, to a clone of ebay. This is done with a href code in html coding. I will show you an example. Click on this link:
Look at the link here. It looks as valid as it could. It is written http://signin.ebay.com, but this written link actually points again, yes, to a clone of ebay. This is done with a href code in html coding. I will show you an example. Click on this link: This whole email was actually an image which referred you to a scam website if you clicked anywhere on it. Your mouse cursor changed to a "hand", if you have this set as default when you point over a link.
This whole email was actually an image which referred you to a scam website if you clicked anywhere on it. Your mouse cursor changed to a "hand", if you have this set as default when you point over a link.


